Software berlisensi ini dapat digunakan untuk memonitor devices,switch,server sebagai berikut :
-Check Point Firewalls
-Juniper,NetScreen Firewall
-Cisco Devices – PIX/ASA/FWSM/VPN Concentrator
-Microsoft ISA Server
-CyberGuard
-Fortinet Firewalls
-WatchGuard Firebox
-Snort
-Secure Computing Sidewinder
-SonicWALL Internet Security Appliances
-dll
Pada instalasi ini Windows 2003 R2 Server sudah terinstall, file .EXE installasi Firewall Analyzer sudah didownload dengan lisensi unlimited client.
Windows Service:
Ensure that the Firewall Analyzer application is installed as Windows Service. When you install with single click, by default it will be installed as Windows Services. If you have
carried out custom installation, and chose not to install the application as Windows Service, carry out the procedure to convert the application installation as Windows Service. After this, carryout the following procedure to start as Windows Service.
• Go to the Windows Control Panel, Select Administrative Tools > Services.
• Right-click ManageEngine Firewall Analyzer 7, and select Stop in the menu.
• Alternatively, select Properties. The <Service> Properties screen opens up.
• In the General tab of the screen, check the Service status is “Started” and Stop button is in enabled state and other buttons besides are grayed.
• Click Stop button to stop the windows service.
Firewall Analyzer is essentially a firewall, VPN, and proxy server log analysis tool that collects, stores, and reports on logs from distributed firewalls, and proxy servers on the
network.
Once the server has successfully started, follow the steps below to access Firewall Analyzer.
1. Open a supported web browser window
2. Type the URL address as http://<hostname>:8500 (where <hostname> is the name of the machine on which Firewall Analyzer is running, and 8500 is the default web server port)
3. Log in to Firewall Analyzer using the default username/password combination of admin/admin.
Firewall Analyzer provides two more external authentication apart from the local authentication. They are Active Directory authentication and Remote Authentication Dial-in User Service (RADIUS) authentication. If you import users from Active Directory or if you add a RADIUS server details, you will find the Options >> link besides the Login button in the Firewall Analyzer Client UI Login screen. If you click the Options >> link, Log on to field will appear below the Password field. The Log on to field will list the following options:
• Local Authentication – If the user details are available in local Firewall Analyzer server user database
• Radius Authentication – If the user details are available in RADIUS server and dummy user entry should be avilable in local Firewall Analyzer server user database
• Domain Name(s) – If the details of the user of a domain is imported from Active Directory into the local Firewall Analyzer server user database Enter the User Name and Password.
License Information
After you log in to Firewall Analyzer, click the Upgrade License link present in the topright corner of the screen. The License window that opens, shows you the license information for the current Firewall Analyzer installation.
The License window displays the following information:
• Type of license applied – Trial or Registered (Professional, Premium)
• Product version number
• Number of days remaining for the license to expire
• Maximum number of devices that you are allowed to manage Upgrading your License
Before upgrading the current license, make sure you have the new license file from ZOHO Corp. saved on that system.
1. Browse for the new license file, and select it.
2. Click Upgrade to apply the new license file.
The new license is applied with immediate effect.
Configure Your Firewall
If your firewall is capable of exporting logs to the displayed ports in Firewall Analyzer, then set the appropriate parameters in the firewall to do so. Click the How do I do
this? link for specific instructions on setting up log exports on certain firewalls.
Add Syslog Server
If your firewall cannot export logs to the displayed ports in Firewall Analyzer, but can
export logs to another port, click the Add Syslog Server link to add a virtual syslog
server and start receiving exported logs on the newly configured port.
Import Log File
If your firewall cannot export logs, or you need to generate reports from a squid proxy
server click the Import Log File link to import a log file from the local machine or a
remote machine via FTP.
Simulate
If you do not want to receive log files from any device, but still generate reports, click
the Simulate link to generate reports from sample firewall logs. You can later turn this
off by clicking the Stop Simulate link from the Settings tab.

Live Reports
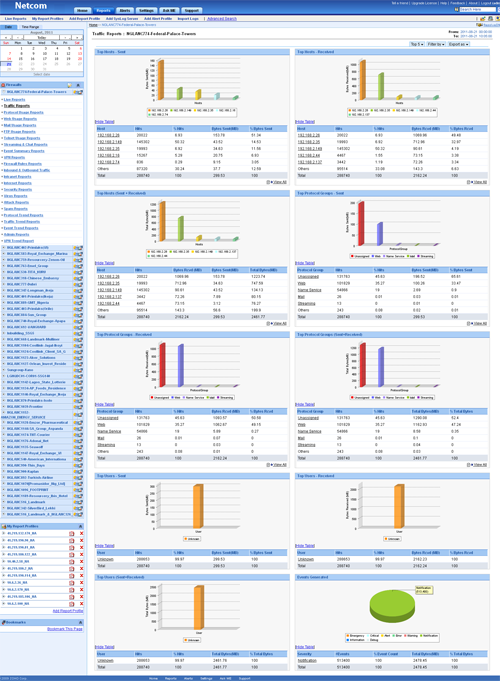
The Live Reports provide a live visual representation of the traffic load across network links. Graphs are similar to that of MRTG, with the aim of providing a simple way to see exactly how much inbound and outbound traffic was generated for each device.
• Interface/Zone Reports For all devices
• Live Reports of Each Firewall Device
• Live Reports of Each Squid Device
Interface/Zone Reports (Live Reports For all devices) Click the Interface/Zone Reports link in the sub tab to see the Interface wise live reports for all devices, for the last 24 hours, over a 5-minute average.
Interface/Zone Live Reports Dashboard (Last 24 Hours) screen opens up. In that screen you will find Device – Interface details table. It will list all the devices and their interfaces. Click the Show All link or + tree icon to the left of the device in the list.
Hide All link or – tree icon will display the list of devices and the numbers of interface the device has. The expanded table lists the Device Name, Interface Name, Bandwidth IN, and Bandwidth OUT. Bandwidth IN and Bandwidth Out will display the bandwidth usage of the interface in percentage and the average speed in Kbps.
Click on the Live Reports link below the device in the list to view the live reports for that device alone.
Click on the individual interfaces names of the device in the list to view the only the live reports of the interface of the device.
Configure SNMP protocol settings for your Firewall device
The procedure to configure the SNMP protocol settings of Firewall devices in the Firewal Analyzer is given below:
• Click Interface/Zone Reports > Click Configure SNMP protocol for Live reports. “Try now.” link. Add Live Settings page appears.
• In that, the devices are listed in the Device Name drop down list. Select the device as required.
• Below the Device Name, the IP Address of the selected device will appear.
• Select the SNMP Version V1 or V2 or V3 using the respective radio button.
o Version 1 (V1):
o Enter the SNMP Community of the device in the text box
o Enter the SNMP Port of the device in the text box
o Version 2 (V2):
o Enter the SNMP Community of the device in the text box
ManageEngine Firewall Analyzer 6.0 :: Help Documentation
o Enter the SNMP Port of the device in the text box
o Version 3 (V3):
o Enter the SNMP Community of the device in the text box
o Enter the SNMP Port of the device in the text box
o Enter the User Name of the device in the text box
o Enter the Context Name of the device in the text box
o Authentication:
o Select the Protocol for authentication from the drop down list (MD5, SHA).
o Enter the Password for authentication in the text box
o Encryption:
o Select the Protocol for encryption from the drop down list (DES, AES).
o Enter the Password for encryption in the text box
• Select the reports in the Select Reports section. In that section, the Report Name and Protocol are listed.
• Select Interface Live Report using the check box. Select the Protocol for the report. On selecting the Interface Live Report, Interval field will appear with the drop down list. You can select 1 minute or 5 minutes or 10 minutes granularity in Live reports by choosing appropriate interval.
• Select Live VPN Users report using the check box. Select the Protocol for the report. This report will be listed only if the device has the provision to get the Live VPN Users using SNMP protocol. Otherwise, this report option will not be there.
• The Apply to other similar devices section, contains list of devices of the same vendor type as the selected device with the check boxes to select, along with Select All devices option. If you want to apply the same credentials (Community, Port, etc.,) to other similar firewalls, please select them.
• Click Save button to save the configuration and Cancel button to cancel the operation. Upon saving the form, the details are stored in the database and a sample SNMP query is made to test connection. If SNMP query is not successful, error message will be displayed on top of the page. Upon error, ensure the credentials provided are correct. Also ensure you have provided Management access through the source interface for SNMP protocol. Once the ‘Live Settings’ is added successfully, the Edit | Disable | Delete SNMP options are displayed to respective devices in Interface Live Reports Dashboard. The Live Reports and Interface Live Reports are populated with SNMP data.
Using the SNMP parameters configured, all the devices will be queried to get interface details. To configure/enable SNMP protocol in individual Firewall devices, refer the respective device configuration documents. Fortigate, Netscreen, Cisco PIX, Cisco ASA, Cisco Firewalls using ASDM tool ZOHO
Configuring SNMP parameters for specific interfaces
Before the interface name, you will find icon. Click the icon to set the Interface Details specific to this interface. Configure Interface Details screen pops-up. On the top you will see two options, one is User Input and the other is Get from SNMP query with radio buttons. By default User Input radio button is selected. If you want to manually enter the interface details, carryout in this screen as given below: In the User Input screen, Device Name, Interface Name will be displayed. Besides the name of the interface, you will find edit icon. Click the icon to change the interface name as per your requirement. The result will take effect immediately. You can enter the Interface IP, Interface IP, Up Link Speed (in Kbps), and Down Link Speed (in Kbps) values manually. Select the Get from SNMP query radio button if you want the application to automatically query the interface through SNMP and fetch the interface details. In the
Get from SNMP query screen, Device Name will be displayed and you can enter the Device IP Address, SNMP Community and SNMP Port. Enter the the SNMP Community and SNMP Port parameters. Using the SNMP parameters configured, the specific interface will be queried to get interface details.
Click Save button to save the configuration and Cancel button to cancel the operation.